What are Two Different Types of Denial of Service attacks
TYPES OF ATTACK
- SYN FLOOD : They are concept-based Denial of Service attacks and rely on the 3 way handshake, filling up a table known as the TCB. TCB or the Transmission Control Block is a transport protocol data structure that holds all the information about a connection.
When the server receives the initial SYN packet from the client, it creates an entry in the TCB. The server then responds with the SYN+ACK packet and hopes that the client would send an ACK packet as soon as it receives the SYN+ACK. The connection is in a TIME_WAIT() status, as long as the server waits for the final packet from the client. If the ACK packet is not received by the server in some time, it believes that it has been lost somewhere in the network, thus it sends another SYN+ACK packet. Finally if after multiple retries, none of the SYN+ACK packets are acknowledged by the client, the session is closed, and this time duration is around 30 seconds.
During this time period, it is possible to send thousands of SYN packets to a server, thus creating a large number of entries in TCB, making it overloaded, and not accepting any new connection. So now, even when a legitimate user would be sending his SYN packet, it would be ignored, as there is no more space left in the TCB.
To generate this kind of attack, the hping3 utility could be used.
hping3 –rand-source –S –L 0 –p [target port] [target IP]
2. ICMP Flood: An ICMP Flood or Ping flood or a Smurf Attack is one of the most popular ways of carrying out DoS attacks on the internet. In this attack, the attacker sends large amounts of ICMP packets (or sometimes by sending oversized packets) in order to crash the TCP/IP stack (TCB) of the server machine
- Teardrop Attack : This attack utilizes a bug in the OS itself for causing a Denial of Service. This attack usually affected Windows 3.1, 95 and NT machines and also Linux versions previous to 2.0.32 and 2.1.63. The bug causes the TCP/IP fragmentation re- assembly code to improperly handle overlapping IP fragments. The packets are forged to overlap over each other, where the host tries to reassemble them causing a
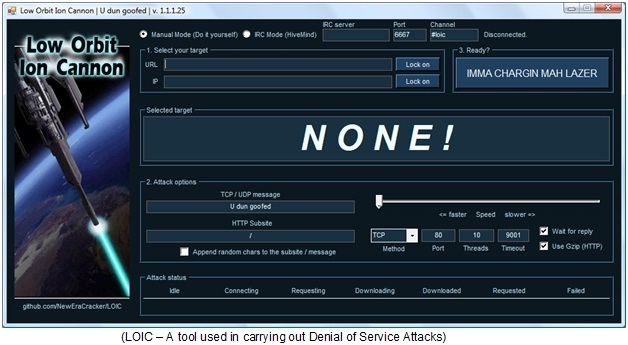
These were some of the important methods of performing Denial of Service Attacks. However, the methods are not limited to only these three. The student should go ahead and read for more methods of performing DoS Attacks. With the increase in tools approach, these days Denial of Service attacks could be easily performed by any script kiddy. One of such tools is LOIC or Low Orbit Ion Cannon. It is an open-source tool, coded in C# and designed for network stress testing by penetration testers.
However, this tool has been recently used by a large group of hackers, for carrying out DoS attacks (or DDoS when used by multiple persons) against big corporations, most of them landing behind the bars finally.








1 Comment
It抯 really a great and useful piece of info. I抦 happy that you shared this useful information with us. Please keep us up to date like this. Thanks for sharing.