What is Cross-Site Scripting
The second most commonly exploited web vulnerability is Cross-Site Scripting (SQL Injection being the first). Cross-Site Scripting, also known as XSS is an injection type web application vulnerability, which occurs mainly when a web application allows the user-supplied data to be actively displayed and rendered on a webpage without proper escaping or encoding.
Unlike SQL Injection, this vulnerability affects the user instead of the web application. In this chapter, we will understand what Scripting is, and then move on to Cross-Site Scripting Attacks.
Scripting
Gone are the days when the websites were pure static pages in pure HTML pages. Present-day websites are driven by dynamic content, with JavaScript (or VBScript) being used along with HTML. Scripting is enabled by default in most browsers, to have a better sense of interaction with the user.
The JavaScript is run at the client-side on the browser to provide interactivity to the user.
However, in some cases, it may pose a security risk too, where malicious scripts are embedded on behalf of legitimate websites, to compromise the user’s security.
Lets take a legitimate example, where the content of a webpage is modified using Javascript :
<html>
<head>
<script type=”text/javascript”>
function hello(){
document.write(“Hello World”);
}
</script>
</head>
<body>
<h1>Test Web Page</h1>
<button type=”button” onclick=”hello()”>Hello</button>
</body>
</html>
When the web browser would run the webpage, we would get the webpage to be like this.
On clicking the button, it will display the text “HelloWorld”. This is the most basic example of Scripting using Javascript functions.
Just like this example, in Cross-Site Scripting attacks, a script is used to perform malicious actions on behalf of the user. To add more, the spams, which you get to see on famous Social Networking websites these days, most of them are an example of XSS.
Attack Overview
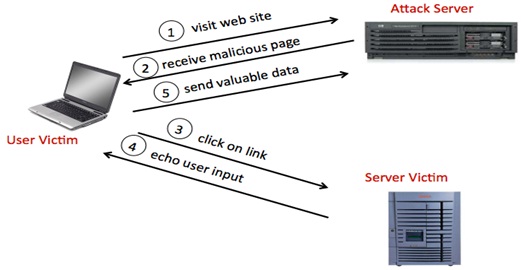
Cross-Site Scripting attacks are flaws in the website, that allow client-supplied data to be used in the web application without proper encoding or escaping. Attackers embed their scripts in webpages, which returns the embedded content without any modification, thus making the script to be executed on the client-side.
The expression “cross-site scripting” originally referred to the act of loading scripts from third-party web applications to a targeted domain.
An XSS could be used by an attacker to :
• Steal the cookies of an authenticated user
• Capture the key logs of the user
• Screen and CursorJacking
• Getting full access to the client’s system
• BlackHat Advertising
• Website Defacement
• Immediate Redirect to a malicious website
Cross-Site Scripting attacks usually take place in two steps –
a. A malicious request is sent to the webserver
b. The web server then responds with the supplied input without properly encoding it, thus allowing the script to execute in the client’s browser.
Following is a graphical representation of a Cross-Site Scripting attack in progress:
Wireless and Web Pentesting
Course Description Network Penetration Testing course for beginners taking you from wondering what hackers do to set up a lab, learning Kali Linux, and…
Advance Ethical Hacking and Penetration Testing
Overview Ethical hacking is an extremely valuable job skill that the more applications, the more website, the more software that is created, the more…
Ethical Hacking and Penetration Testing
Overview Ethical hacking is an extremely valuable job skill that the more applications, the more website, the more software that is created, the more…
Advanced Python Scripting for Ethical Hackers
Many of the most powerful, memorable and effective photographs are black and white images. With digital photography though you can no longer take a…
Network Pentesting
Course Description @ Network Pentesting course for beginners taking you from wondering what hackers do to set up a lab, learning Kali Linux, and…
Proactive Cybersecurity for Individuals and Small Businesses
How You Can Protect Your Identity While Surfing Online, Starting Today…In This Step by Step Video Course While 99% of the population won’t do…
Python for Ethical Hackers
Many of the most powerful, memorable and effective photographs are black and white images. With digital photography though you can no longer take a…
Wireshark Network Analysis
Sass is completely compatible with all versions of CSS. We take this compatibility seriously, so that you can seamlessly use any available CSS libraries.
Vulnerability Assessment
Less is a CSS pre-processor, meaning that it extends the CSS language, adding features that allow variables, mixins, functions and many other techniques that…