What is Post Method XSS Cross-Site Scripting Attack
POST METHOD XSS
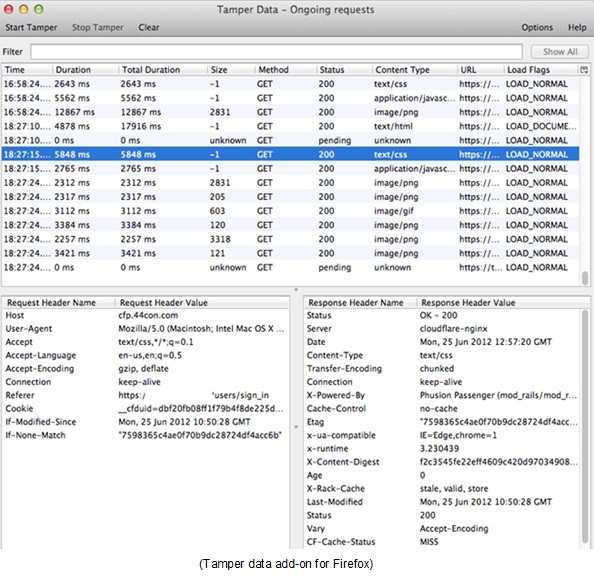
Cross-Site Scripting attacks could also be triggered when the data is being sent with a POST method instead of the usual GET.
We can use a Firefox add-on named “Tamper Data” or any other packet sniffer to manipulate the POST values and insert our XSS query into the POST value.
Beef (Browser Exploitation Framework)
A lot has been discussed over what could be done using Cross-Site Scripting. One way to take over the complete control of the victim using XSS is through the use of XSS Shell.
However, recently, a tool called BeeF (Browser Exploitation Framework) has been released to gain complete control of the system of victims, using a Cross-Site scripting vulnerability)
Generally in Cross-Site Scripting attacks, the attacker usually inserts a script as a payload to get the victim’s cookies or pops up an alert box. Using Beef, in XSS vulnerability, an attacker just has to insert the Beef server’s URL, listening on the attacker’s machine. As soon as the victim navigates to that page, using a JS redirection or clicking on the link, he is in complete control of the attacker.
Wireless and Web Pentesting
Course Description Network Penetration Testing course for beginners taking you from wondering what hackers do to set up a lab, learning Kali Linux, and…
Advance Ethical Hacking and Penetration Testing
Overview Ethical hacking is an extremely valuable job skill that the more applications, the more website, the more software that is created, the more…
Ethical Hacking and Penetration Testing
Overview Ethical hacking is an extremely valuable job skill that the more applications, the more website, the more software that is created, the more…
Advanced Python Scripting for Ethical Hackers
Many of the most powerful, memorable and effective photographs are black and white images. With digital photography though you can no longer take a…
Network Pentesting
Course Description @ Network Pentesting course for beginners taking you from wondering what hackers do to set up a lab, learning Kali Linux, and…
Proactive Cybersecurity for Individuals and Small Businesses
How You Can Protect Your Identity While Surfing Online, Starting Today…In This Step by Step Video Course While 99% of the population won’t do…
Python for Ethical Hackers
Many of the most powerful, memorable and effective photographs are black and white images. With digital photography though you can no longer take a…
Wireshark Network Analysis
Sass is completely compatible with all versions of CSS. We take this compatibility seriously, so that you can seamlessly use any available CSS libraries.
Vulnerability Assessment
Less is a CSS pre-processor, meaning that it extends the CSS language, adding features that allow variables, mixins, functions and many other techniques that…