What is Twitter Wipe Address Book Vulnerability
Twitter allowed deletion of a user’s address book, by the user, with just a click of a single click URL. However, Twitter didn’t check if the request came actually from the user, or the user has been tricked to visit that link.
The process to be followed is :
1. A user logs into mobile.twitter.com
2. If he wants to delete his address book, he would click on Delete Address Book under settings.
3. Upon clicking, a GET request is sent to
“https://mobile.twitter.com/settings/wipe_addressbook”
4. A message is presented that the user’s contacts have been removed.
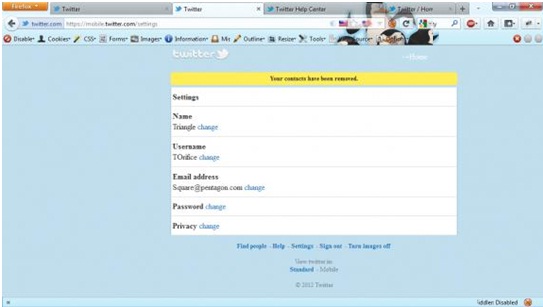
So, in the absence of the security token for validation, an attacker could just make the user visit a particular URL, and all the contacts of the user would be deleted.
This vulnerability was discovered by one of my friends, Riyaz Ahmed Walker, who also got credited in the Twitter Security List (http://twitter.com/about/security) for finding this vulnerability.
Wireless and Web Pentesting
Course Description Network Penetration Testing course for beginners taking you from wondering what hackers do to set up a lab, learning Kali Linux, and…
Advance Ethical Hacking and Penetration Testing
Overview Ethical hacking is an extremely valuable job skill that the more applications, the more website, the more software that is created, the more…
Ethical Hacking and Penetration Testing
Overview Ethical hacking is an extremely valuable job skill that the more applications, the more website, the more software that is created, the more…
Advanced Python Scripting for Ethical Hackers
Many of the most powerful, memorable and effective photographs are black and white images. With digital photography though you can no longer take a…
Network Pentesting
Course Description @ Network Pentesting course for beginners taking you from wondering what hackers do to set up a lab, learning Kali Linux, and…
Proactive Cybersecurity for Individuals and Small Businesses
How You Can Protect Your Identity While Surfing Online, Starting Today…In This Step by Step Video Course While 99% of the population won’t do…
Python for Ethical Hackers
Many of the most powerful, memorable and effective photographs are black and white images. With digital photography though you can no longer take a…
Wireshark Network Analysis
Sass is completely compatible with all versions of CSS. We take this compatibility seriously, so that you can seamlessly use any available CSS libraries.
Vulnerability Assessment
Less is a CSS pre-processor, meaning that it extends the CSS language, adding features that allow variables, mixins, functions and many other techniques that…